Europol's first report on the most threatening criminal networks active in the EU, unveils the presence of 821 dangerous criminal gangs across the EU, primarily engaged in drug trafficking and other illicit activities. These organizations operate transnationally, posing significant challenges to law enforcement. Efforts to combat them require enhanced coordination and initiatives to protect legal officials from intimidation and bribery.
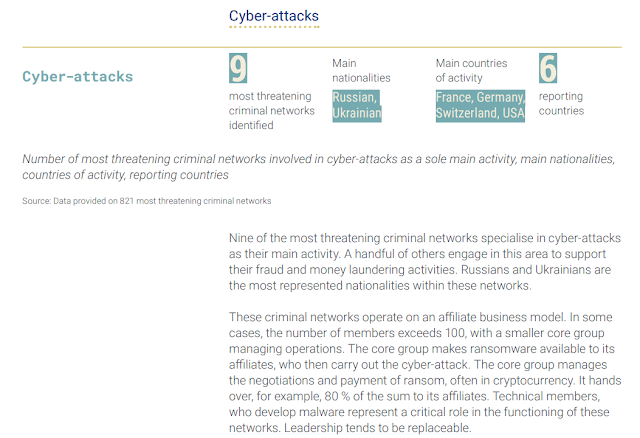
There is a special section dedicated to Cyber-Attacks (pag 36) that highlights the disruption of lockbit ransomware group as case example:
- Agile: The most threatening criminal networks exhibit remarkable agility. (pag 10).
- LBS: Legal Business Structures. 86% of the most threatening criminal networks make use of LBS.
- Some sectors particularly at risk; all sectors potentially affected: Three sectors are particularly affected by criminal infiltration or abuse: construction, hospitality and logistics (i.e. transport and import/export companies). The data show clearly that LBS are infiltrated or misused by criminal networks across almost all sectors, including tourism, recycling, wellness and sports, retail and cultural associations.The data show clearly that LBS are infiltrated or misused by criminal networks across almost all sectors, including tourism, recycling, wellness and sports, retail and cultural associations.
- The most threatening criminal networks in the EU use real estate as one of the main industries to launder their illicit profits (41 %).
- Main nationalities of the criminal networks are: Albania, Belgium, France, Germany, Italy, the Netherlands, Poland, Spain, Türkiye and Ukraine. Most criminal networks are made up of both EU and non-EU nationals.
- 82% focus on one criminal activity, such as drug trafficking or organised property crime. The remaining 18% are truly poly-criminal networks active in multiple main crime areas.
- Frauds (mainly investment and romance): is the second most common activity of the most threatening criminal networks. (pag 30).
- Money laundering activities take place in more than 80 countries. (pag 45)
- The criminal networks that use countermeasures against law enforcement strategically as part of their day-to-day operations mostly use technologies such as encrypted applications or devices (EncroChat or SkyECC) on which they use code language to communicate.
- Cyber expertise required: Cyber-service and technological solution providers offer critical support to networks involved in fraud schemes. Specifically, they devise mass mailing and phishing campaigns, create fake websites, advertisements and social media accounts, and support other cyber-based processes related to investment frauds and online fraud schemes. Networks involved in cyber-attacks play a critical role in programming malware, ransomware and hosting botnets. These individuals also occupy a crucial position in networks engaged in drug trafficking, extortion and racketeering and money laundering. They support the networks by advising them on online means for the movement of money and cryptocurrency payments (pag 56).